See what hackers see. Fix what they’d exploit.
Aftra identifies actionable opportunities to enhance your cybersecurity strategy through vulnerability monitoring and detection.
The importance of real-time vulnerability detection and monitoring.
Unlike basic scanners and one-time audits, Aftra enables continuous vulnerability management, helping you stay ahead of evolving threats. It’s like having an ethical hacker on your team 24/7, monitoring your environment and catching security weaknesses as they appear.
More than a vulnerability scanner.
Benefit from the best coverage out there with monitoring that combines hacker methodologies with actionable insights.
Real-time threat detection.
Get more than a snapshot of assets. Our technology continuously runs in the background picking up vulnerabilities in real-time.
Identify opportunities for improvement.
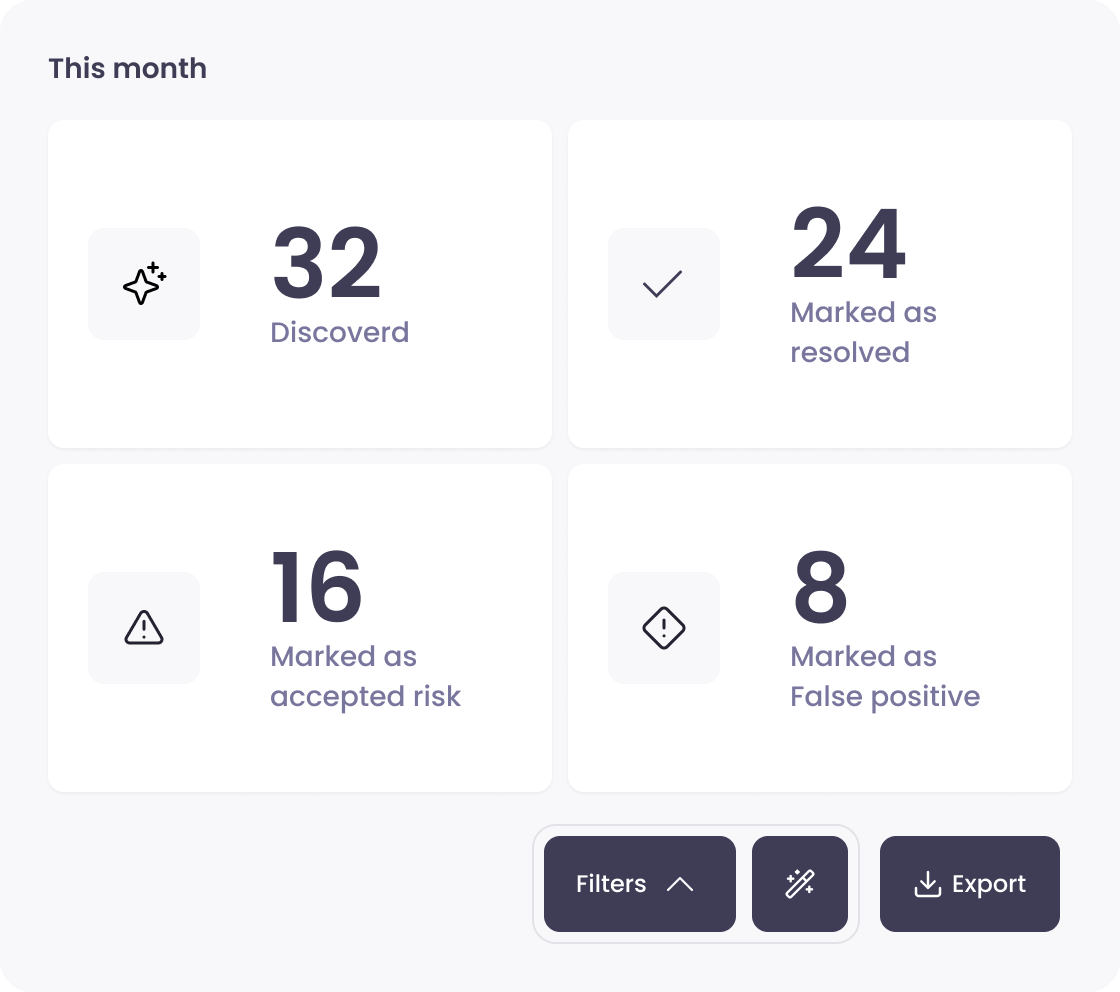
Aftra provides actionable opportunities to improve security, prioritized by severity and complete with remediation guidance.
Continuous vulnerability management with the best scanners out there.




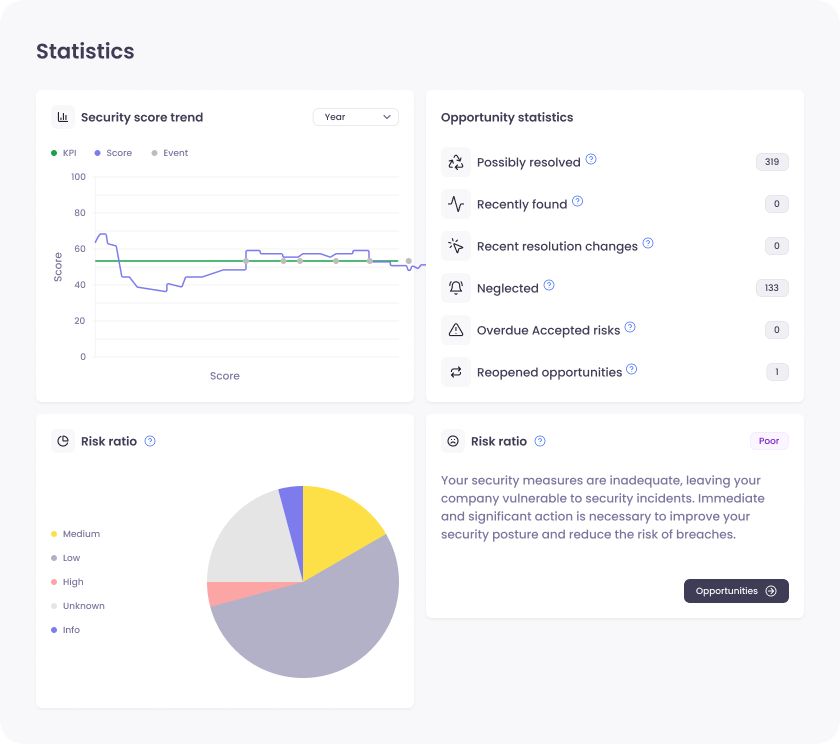
From vulnerability management to KPI driven security
Cybersecurity is more than just finding and fixing vulnerabilities. It’s about clear goal setting and tracking from the top down. Aftra gives executives the tools and vocabulary they need to understand and take responsibility for their organization’s security posture, giving it the place it deserves in board meetings.
With measurable insights, you can track how your security posture improves over time.
Testimonials
Here’s what our customers have to say.
Vodafone
Veritas
INNNES
Insights from the blog
Explore our latest blogs for insights, tips, and tricks about cybersecurity.

From gaming frontlines to supply chain zero-day: A deep dive into software security with Charlie Eriksen
Insights from security expert Charlie Eriksen on the challenges of securing open-source software and supply chains & strategies for defense.

Aftra in review
133k vulnerabilities found and $31M saved for our customers. Read about Aftra’s 2025 highlights, including new API scanning and suggested actions.

How Aftra's badge campaign enhanced customers' cybersecurity resilience
Discover how Aftra's badge campaign enhanced cybersecurity resilience for customers through proactive actions to reduce risk and strengthen defenses.
Dynamic vulnerability management at your fingertips