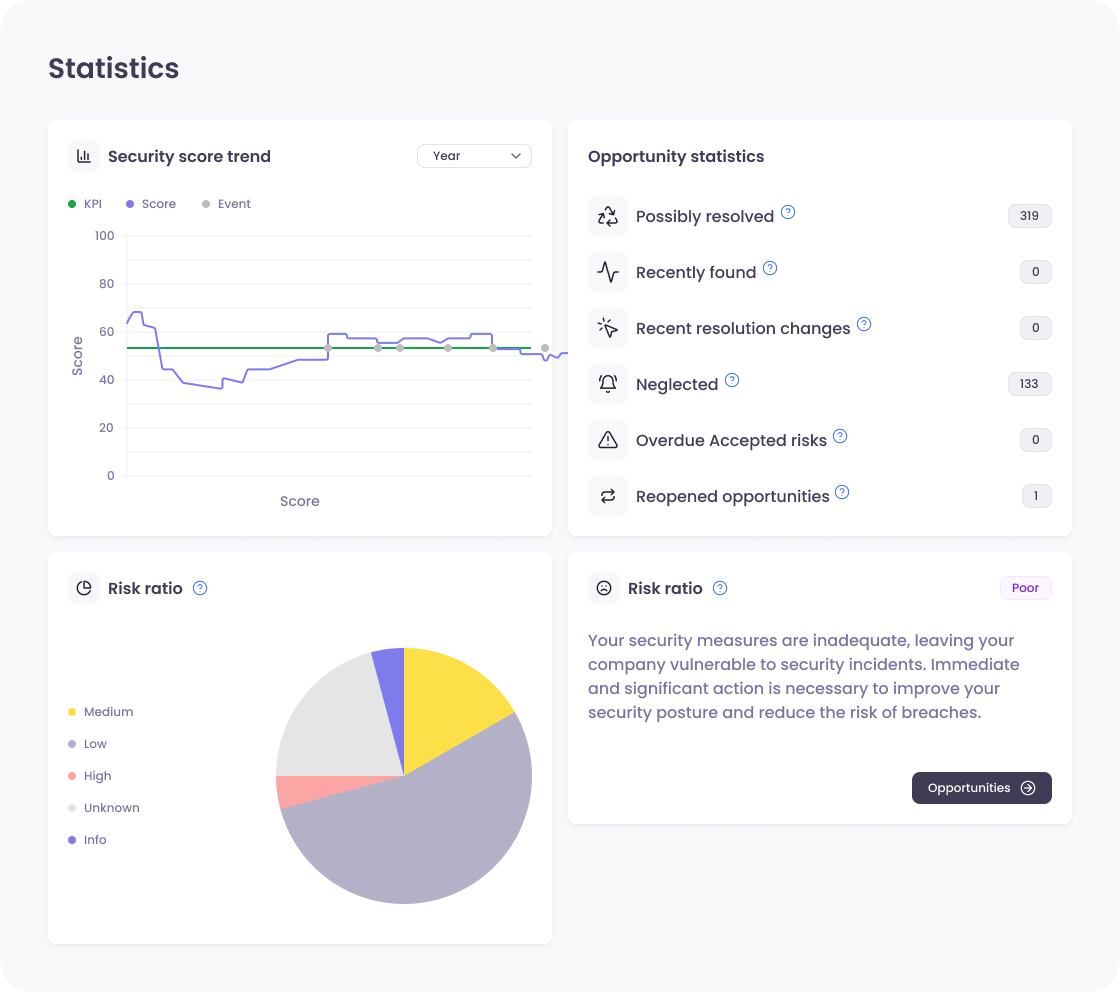
Track your cybersecurity posture with simple, actionable KPIs
Invest in the long-term resilience of your business with the security metrics you need to drive change at your fingertips.
Cybersecurity isn’t complex, executives just lack the vocabulary to understand it and take action.
Keep up with your evolving attack surface.
Understanding your digital footprint and the vulnerabilities associated with it is the first step towards achieving cyber resilience.
Comply with regulatory frameworks such as NIS2.
Executives and boards are now accountable for cybersecurity. Get the tools you need to understand your cyber risk and take action.
Be proactive today to avoid a scandal tomorrow.
Aftra provides the insights necessary to adopt a proactive cybersecurity strategy and address weaknesses before they’re exploited.
Get the key metrics you need to set, track, and manage security goals.
Company attack surfaces constantly evolve. New tools, accounts, and domains appear. Software becomes outdated. Vulnerabilities creep into code. Employees sign up for third-party services using work credentials—often with weak passwords.
Aftra continuously monitors and uncovers these risks and more.



Understand the threats posed to your internal network
Testimonials
Here’s what our customers have to say.
Blue Car Rental
INNNES
Veritas
Vodafone
Insights from the blog
Explore our latest blogs for insights, tips, and tricks about cybersecurity.

From gaming frontlines to supply chain zero-day: A deep dive into software security with Charlie Eriksen
Insights from security expert Charlie Eriksen on the challenges of securing open-source software and supply chains & strategies for defense.

Aftra in review
133k vulnerabilities found and $31M saved for our customers. Read about Aftra’s 2025 highlights, including new API scanning and suggested actions.

How Aftra's badge campaign enhanced customers' cybersecurity resilience
Discover how Aftra's badge campaign enhanced cybersecurity resilience for customers through proactive actions to reduce risk and strengthen defenses.

Your APIs are leaking secrets: what you don't realize you're exposing
Protect your APIs from hidden vulnerabilities. Learn how everyday development practices can expose your systems and how to secure them effectively.

The software supply chain risk you're probably ignoring
We recently spoke with Niels Ingi Jónason, Co-Founder at Ambaga and security engineer on the topic of the software supply chain security. Read more.
Interested to see how secure your digital assets are?