Simple & actionable cybersecurity
Don't just scan for vulnerabilities. Understand what's at risk and manage it.
Stay ahead of cyber threats and protect sensitive company information through KPI-driven cybersecurity.
90% of security breaches are preventable, you just need to know how.
Testimonials
Here’s what our customers have to say.
Vodafone
Veritas
INNNES
Securitas
Blue Car Rental
Bridging the gap between executives, IT & security
We make the complex world of digital security simple for everyone involved.
Stay ahead of threats and gain peace of mind.
New regulations like NIS2 and DORA can hold executives personally accountable for cyber incidents.
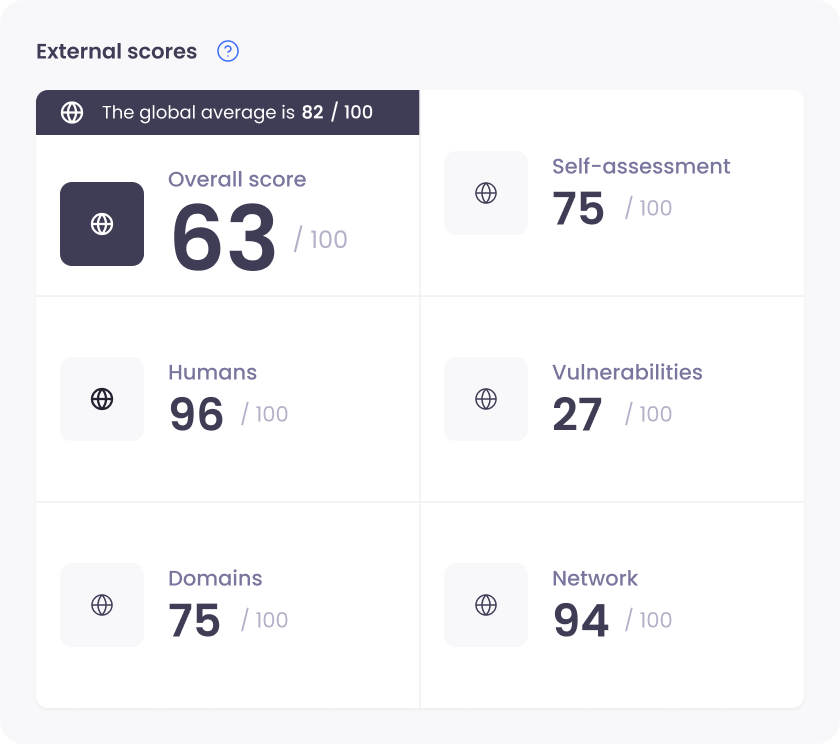
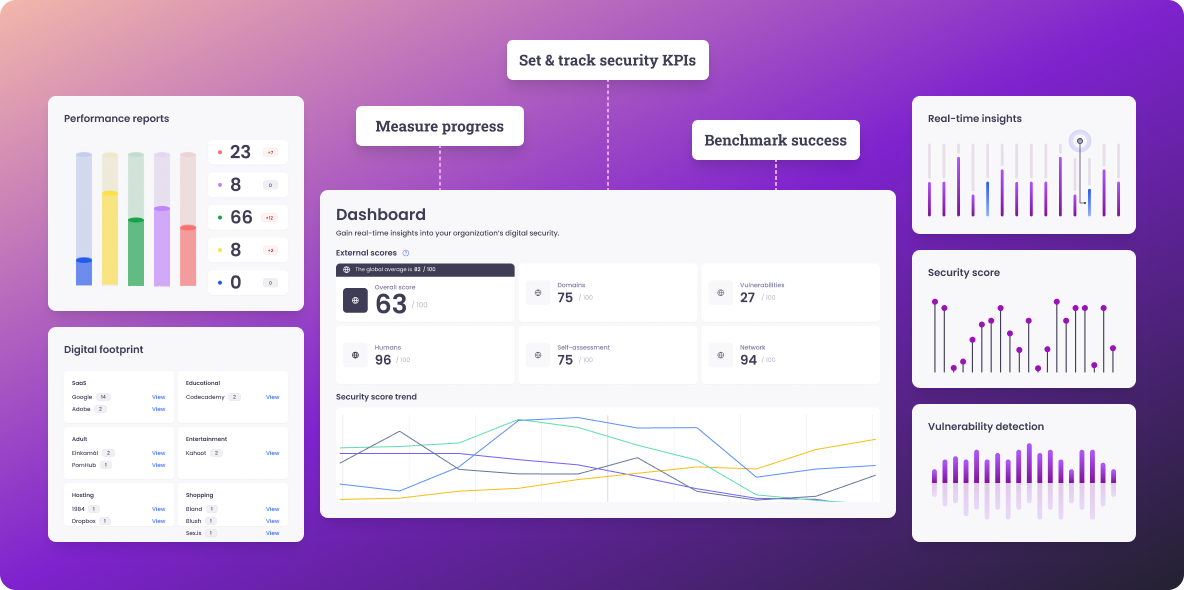
Our intuitive dashboard enables you to track your security score, set actionable KPIs, and benchmark your organization’s security resilience.
Control of your time without forfeiting security.
New regulations like NIS2 and DORA can hold executives personally accountable for cyber incidents.
Our intuitive dashboard enables you to track your security score, set actionable KPIs, and benchmark your organization’s security resilience.
Don’t let the state of security keep you up at night.
New regulations like NIS2 and DORA can hold executives personally accountable for cyber incidents.
Our intuitive dashboard enables you to track your security score, set actionable KPIs, and benchmark your organization’s security resilience.
Watch how Aftra helps identify and fix vulnerabilities

Why is External Attack Surface Management (EASM) so important?
Empowering you to protect your organization.




Resources to improve security resilience
Explore our guides with insights, tips, and strategies to get started with Attack Surface Management (ASM).

C-suite's role in cybersecurity
Executives now face personal liability for cybersecurity failures. Learn the key terms, threats, and regulations to protect your organization and career.

Management's guide to cybersecurity
Boost your business's cybersecurity, from identifying vulnerabilities to enhancing resilience, with actionable steps and insights to protect digital assets.

The NIS2 Directive
Learn how the NIS2 Directive expands cybersecurity requirements, emphasizing compliance, risk management, and executive accountability to enhance resilience.
Unlock proactive security